https://www.youtube.com/watch?v=YllmY_AqFB0&list=PLyf18hdY22ETbPh-0RtjESZvrrlprOy6M&index=4
Enter the credentials: admin/Admin123
egister SFR with FMC via Command Line
Connect to the parent firewall and open a session with the sfr module;
PETES-ASA# session sfr Opening console session with module sfr. Connected to module sfr. Escape character sequence is 'CTRL-^X'. PETES-SFR login: admin Password:{pasword} Last login: Fri Apr 8 05:04:49 UTC 2016 on ttyS1 Copyright 2004-2015, Cisco and/or its affiliates. All rights reserved. Cisco is a registered trademark of Cisco Systems, Inc. All other trademarks are property of their respective owners. Cisco Fire Linux OS v6.0.0 (build 258) Cisco ASA5506 v6.0.0 (build 1005) >
>show network
>show managers
>show managers
>configure network ipv4 manual 1.1.1.2 255.255.255.0 1.1.1.1
> configure manager delete 10.9.20.25 password123> configure manager add 10.9.20.25 password123
You can then add the FMC as a manager, you will need to supply a registration key.
> configure manager add 10.9.20.25 password123
Manager successfully configured.
Please make note of reg_key as this will be required while adding Device in FMC.
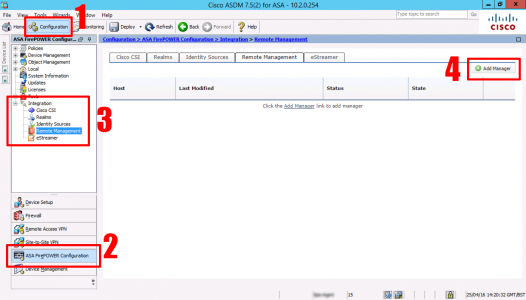
Register SFR with FMC via ASDM
Connect to the ASDM > Configuration > ASA FirePOWER Configuration > Integration >Remote Management > Add Manager.
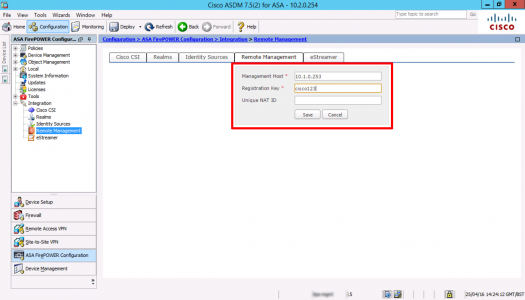
Specify the IP of the FMC Appliance, and registration key > Save.
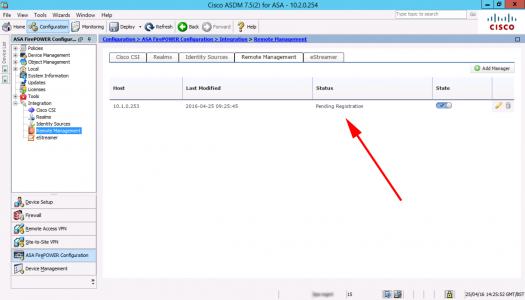
It should then say ‘pending registration’.
Configure the FirePOWER Management Appliance to Accept the SFR Registration
admin/Admin123
>sudo configure-network
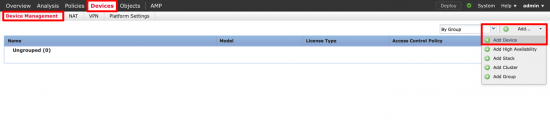
Log into FMC > Devices > Device Management > Add Device.
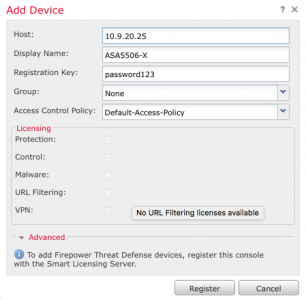
Provide the IP of the SFR module, a display name, the registration key you used above. If you have setup a group you can use it and select your Access Control Policy (dont panic if you have not configured one yet) > Register.
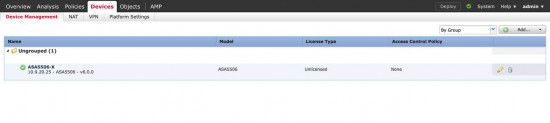
It can take a while, but eventually it should register like so;
Step 5: Add FirePOWER feature licenses in Management Center
In the Management Center, go to System – Licenses and click on Add New License. Follow the same procedure activating licenses outlined earlier.
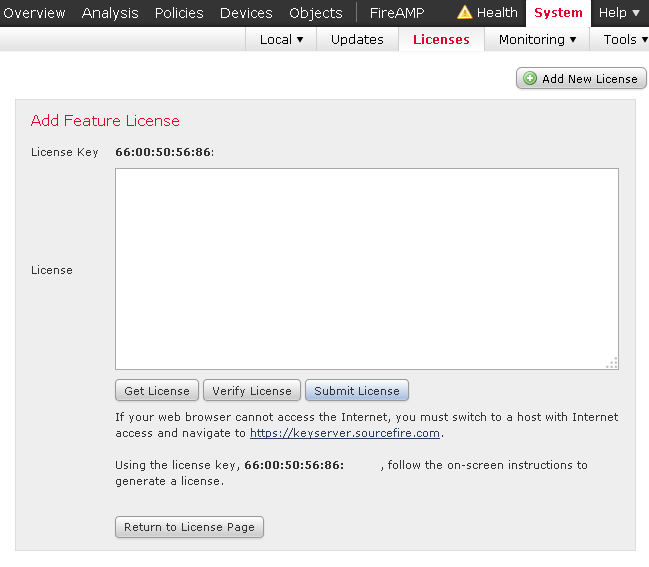
Step 6: Apply licenses to the newly installed FirePOWER module
The Management Center acts as a license repository that manages all the licenses in an organization. A license can be applied to one compatible FirePOWER module at a time. Once the license is used on a FirePOWER module, you may not reuse it on a different module.
To apply the installed licenses to a FirePOWER module, go to Devices – Device Management and click on License. If you have unused and compatible licenses available, you can check the boxes to activate the feature.
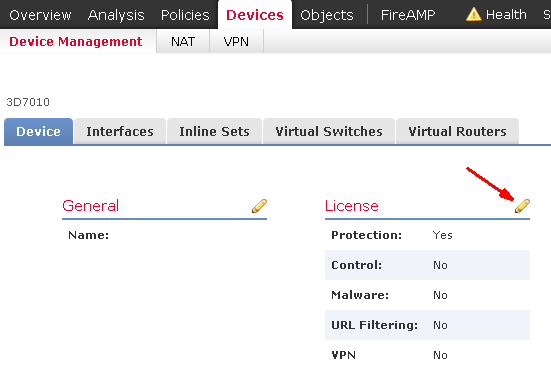
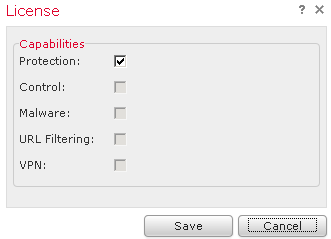
Above example indicates that we only have Protection license available and it has been applied to this device.
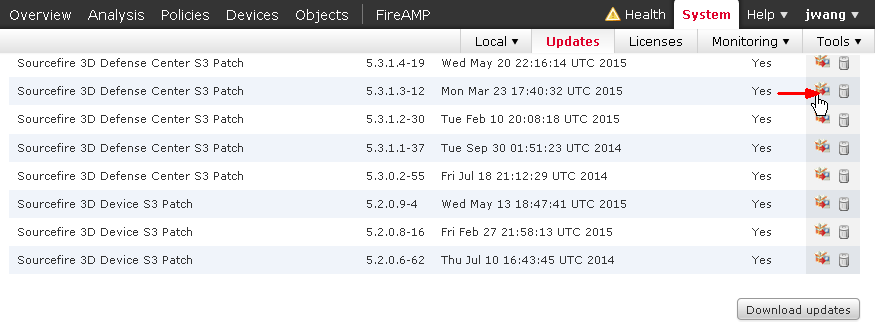
FirePOWER Code Update and Rule Update
It is a good practice to periodically check and run software code updates, security patches. Similar to anti-virus signature updates, FirePOWER’s rule database also need to be updated as soon as the new ones are released.
Run updates in FirePOWER Management Center
One of the benefits of centralized management model is that you only need to download the updates once and push to all compatible FirePOWER modules in the field. To download updates, go to System – Updates. Click on the Download updates button on the lower right corner to make the Management Center to go out to Cisco update center and pull all applicable updates. And you can choose which one you want to install.
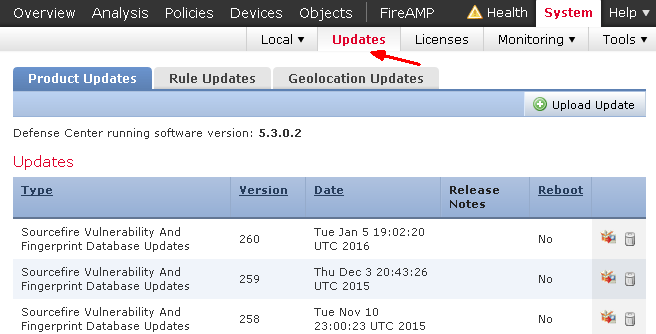
To install an update, click the install icon and select the FirePOWER modules you want to push this update to.
Management IP address for FXOS:
firepower-2110#Scop fabric-interconnect a
firepower-2110 /fabric-interconnect #set out-of-band static/DHCP
DNS Config:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services # create dns
NTP / Time Config:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #set clock
firepower-2110 /system/services #set timezone
firepower-2110 /system/services #create ntp-server
DHCP Server:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #enable dhcp-server
Interface Port-Channel and interface allocation:
firepower-2110# scope eth-uplink
firepower-2110 /eth-uplink # scope fabric a
firepower-2110 /eth-uplink/fabric # create port-channel
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #set clock
firepower-2110 /system/services #set timezone
firepower-2110 /system/services #create ntp-server
DHCP Server:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #enable dhcp-server
Interface Port-Channel and interface allocation:
firepower-2110# scope eth-uplink
firepower-2110 /eth-uplink # scope fabric a
firepower-2110 /eth-uplink/fabric # create port-channel
Https/SSH Service Enable/Disable:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #enable/disable https/ssh-server
FXOS HTTP/SNMP/SSH Access/Restriction:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services # create ip-block
firepower-2110 /system/services # create ipv6-block
FXOS domain Configuration:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services # set domain-name
SYSLOG:
firepower-2110#Scope system
firepower-2110 /system # scope monitoring
firepower-2110 /monitoring # enable/disable syslog
FIPS & Common Criteria:
firepower-2110#Scope system
firepower-2110 /system # Scope security
firepower-2110 /security #enable/disable cc-mode {Common Criteria}
firepower-2110 /security #enable/disable fips-mode {FIPS}
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services #enable/disable https/ssh-server
FXOS HTTP/SNMP/SSH Access/Restriction:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services # create ip-block
firepower-2110 /system/services # create ipv6-block
FXOS domain Configuration:
firepower-2110#Scope system
firepower-2110 /System#Scope Services
firepower-2110 /system/services # set domain-name
SYSLOG:
firepower-2110#Scope system
firepower-2110 /system # scope monitoring
firepower-2110 /monitoring # enable/disable syslog
FIPS & Common Criteria:
firepower-2110#Scope system
firepower-2110 /system # Scope security
firepower-2110 /security #enable/disable cc-mode {Common Criteria}
firepower-2110 /security #enable/disable fips-mode {FIPS}
Local User:
firepower-2110#Scope system
firepower-2110 /system # Scope security
firepower-2110 /security # create local-user / set password
Hostname:
firepower-2110#Scope system
firepower-2110 /System# set name
Session timeout:
firepower-2110#Scope system
firepower-2110 /system # Scope security
firepower-2110 /security # scope default-auth (set session-timeout)
Transparent mode
Hiç yorum yok:
Yorum Gönder